1. base64
在线解密,或是自己写脚本都行
2. Caesar
同上
3. Morse
同上
4. 混合编码
- base64
- html实体编码
- base64
- ascii
5. 不仅仅是Morse
morese解密
得到一串奇奇怪怪的东西
1
MAY_BE_HAVE_ANOTHER_DECODEHHHHAAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA
后面的AB的长度为170
- 5的倍数
- 只有两个字母
- 2^5^为32,可以很方便的表示26个字母
- 所以假设0-25,分别对应a-z
尝试解密看看
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24#分割替换
s="AAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA"
s=s.replace("A","0")
s=s.replace("B","1")
lst=[]
while(s):
lst.append(s[:5])
s=s[5:]
print(lst)
#生成字典
import string
b=string.ascii_lowercase
l1=[]
l2=[]
for i in b:
l1.append(i)
for i in range(26):
l2.append(i)
dic=dict(zip(l2,l1))
print(dic)
#flag
for i in lst:
num=int(i,2)
print(dic.get(num),end="")
6. 幂数加密
1 | #字母数字对应表生成 |
6. easychallenge
给的是一个pyc文件,我就在在线python反编译网站上反编译了一下
得到python原码
1 | import base64 |
emmm,然后就好办了,加密方法都在上面了
1 | import base64 |
7. Normal_RSA
打开附件,里面是pubkey.pem和flag.enc
我们可以利用kali里的openssl来搞
把文件拖虚拟机里
终端输入openssl
openssl rsa -pubin -text -modulus -in warmup -in pubkey.pem- exponent:E
- modulus:N
以上两个要用复制好
上网找在线分解质因数的搞出P,Q
然后在kali中使用(代码如下,pqe自填),会生成一个private.pem
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20#coding=utf-8
import math
import sys
from Crypto.PublicKey import RSA
arsa=RSA.generate(1024)
arsa.p=
arsa.q=
arsa.e=
arsa.n=arsa.p*arsa.q
Fn=long((arsa.p-1)*(arsa.q-1))
i=1
while(True):
x=(Fn*i)+1
if(x%arsa.e==0):
arsa.d=x/arsa.e
break
i=i+1
private=open('private.pem','w')
private.write(arsa.exportKey())
private.close()在终端中打开openssl,输入
rsautl -decrypt -in flag.enc -inkey private.pemojbk
8. 转轮机加密
题目:
1 | 1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE < |
大概就像旧式电话一样
对应着电话号码(2,3,7,5,13,12,9,1,8,10,4,11,6)
把对应轮数中的对应字符(N F Q K S E V O Q O F N P)
拨到第一个去(看下图第一列,与密文相同)
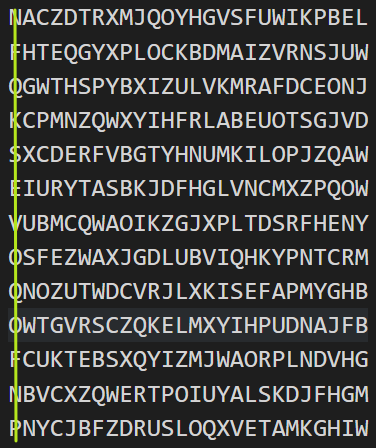
然后竖着看,直到找到有实际意义的字符串
1 | def circle(string,char): |
输出如下
1 | nfqksevoqofnp |
发现就fireinthehole是个可读的字符串
9. easy_ECC
是的,我不会